How google is your enemy if you have no idea what you are doing
10 Jul 2019What is GHDB?
First of all, GHDB (Google Hacking Database) is a collection of google search queries aiming to find vulnerable software without a specific scope/target.
You can find a vulnerability which was crawled by google, as an example, you can find every website which has its home folder indexed, and crawled by Google.
You can find a collection of dorks at exploit-db.
Lets craft some of our own!
Indexed home directories
So for this one, we know the page content and title will say “index of /home/.*” and url will probably contain “home”
Lets try intext: "index of /home" inurl:home intitle:"Index of"
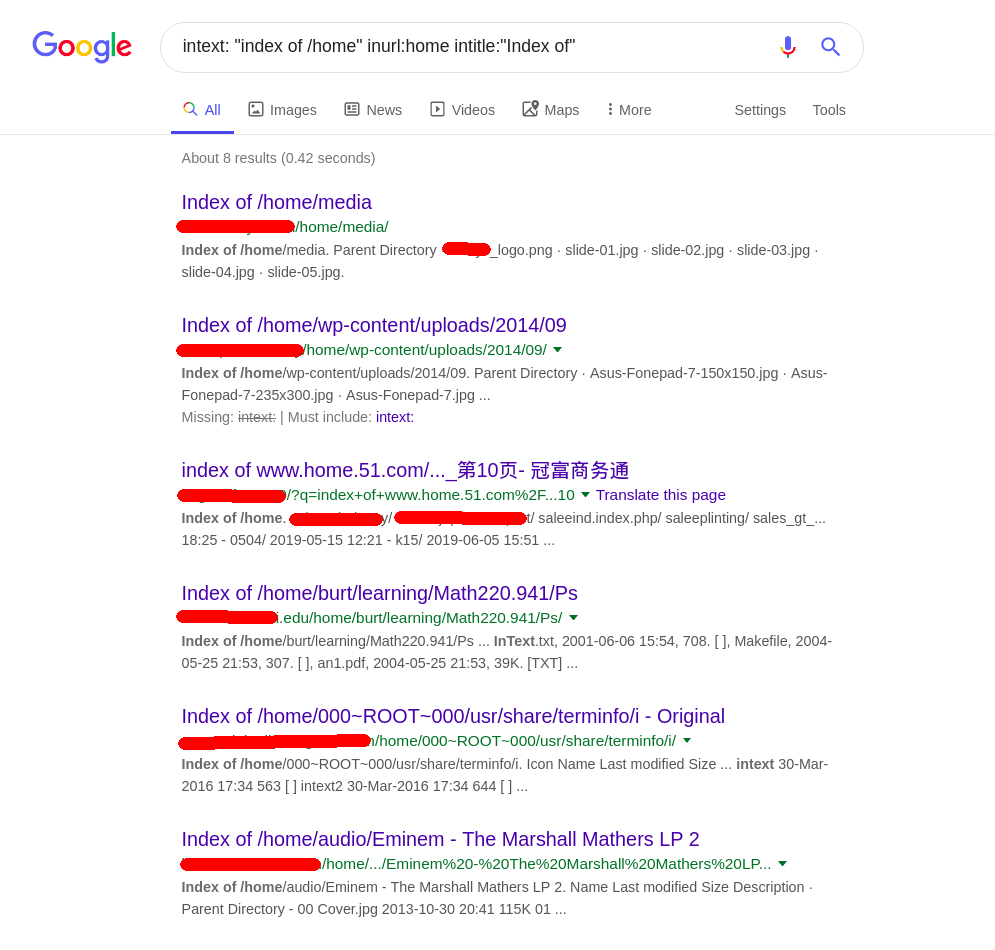
Seems about right…
Reading php config Files
We cant really see the config.php files even if they were crawled, because it shouldn’t expose its source code to the client even if it is cached. However, if they edited it via vi/vim and forgot the swap file, we can read its content.
Lets see all the .config.php.swp files with inurl:".config.php.swp" ext:swp
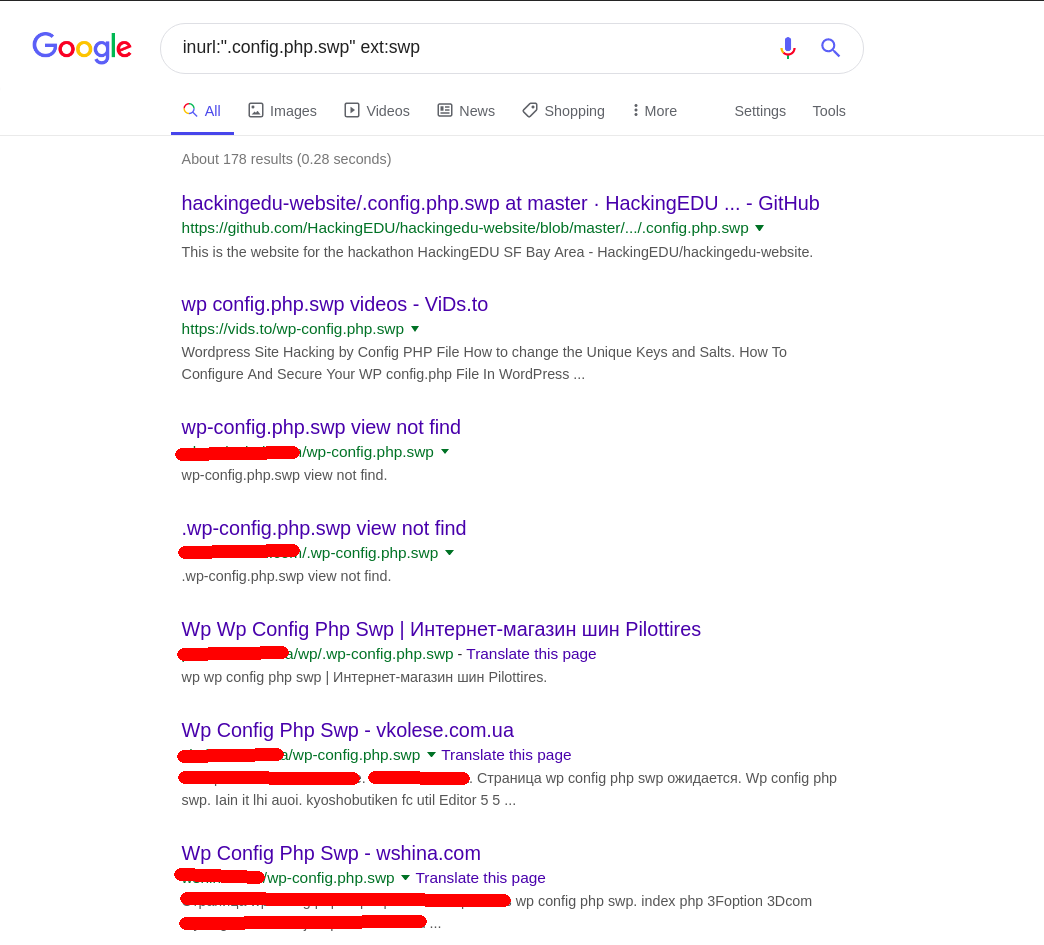
Seems like first two ones are educational pieces about what to do with config.php.swp file, while others seem to be actual swap files.
Bash History
Bash history files can be very powerful. It can reveal linked hosts or if you do the same mistakes as me, you’ll eventually do something like mysql -u user -p mypass and it will be saved on your history file. Its always a good idea to symlink your history file to /dev/null.
Lets see only .bash_history files which were indexed in a folder contents.
intitle:"index.of" intext:".bash_history"
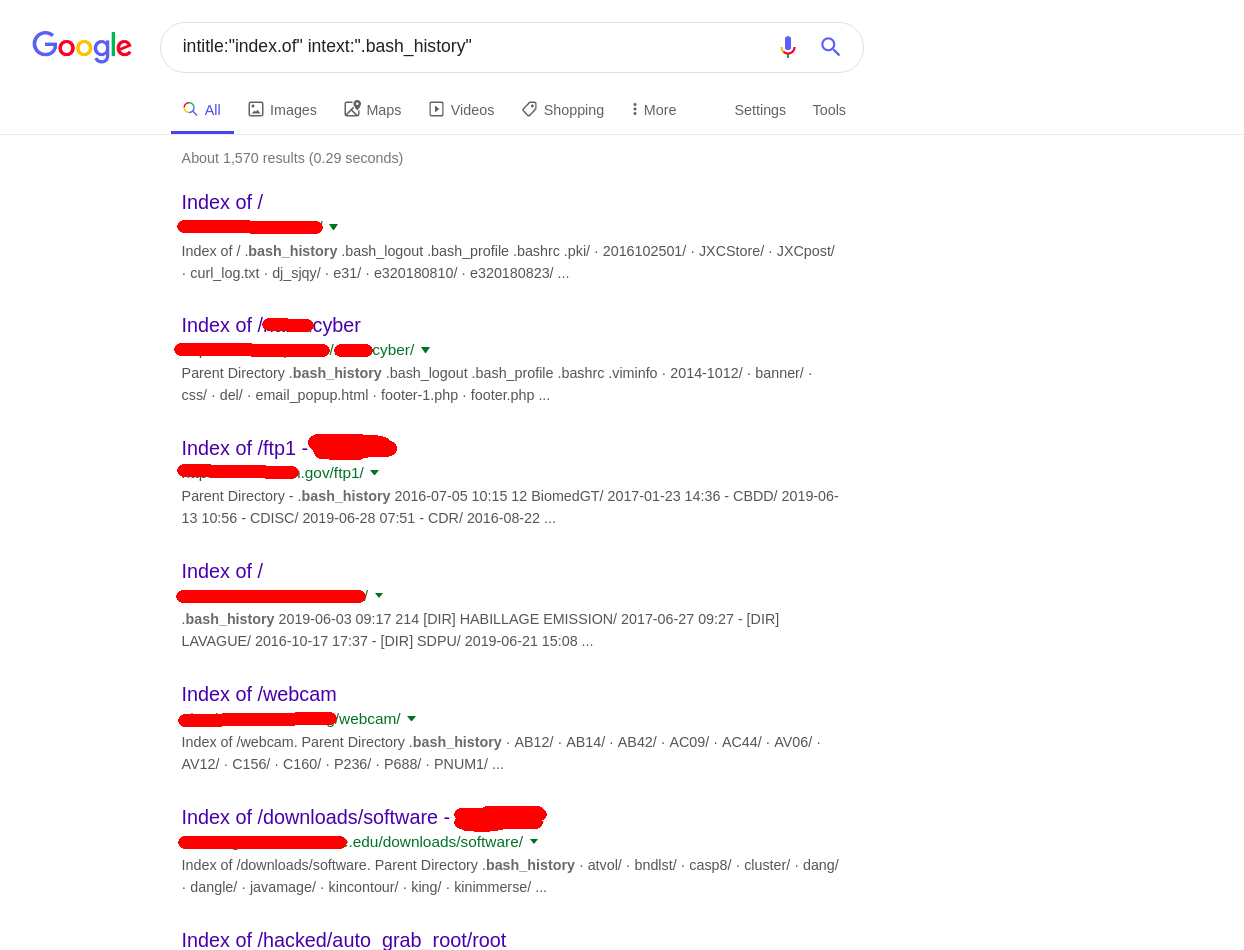
Uuuuhhhhhhh… Thats a .gov 
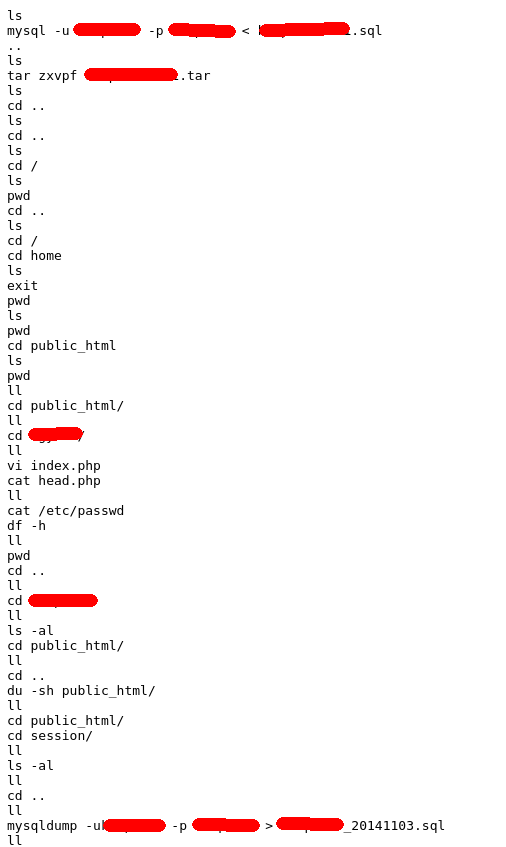
Yeah… I hope to the infosec gods that this is just a honeypot. Also you forgot the space after -u on the dump buddy.
Finding already Pwned boxes
If there is a way to upload/write file to the webroot, there are few tools i know that are used to escalate our situation.
If php is unrestricted, of course we can just drop a shell, but if php is restricted, we may need alternate aproaches. A tool i know for this is reGeorg. It gives you a socks proxy via file upload, which you can use to nmap loopback interface, or to do server side request forgery to bypass .htaccess.
File i use most frequently is tunnel.nosocket.php, so lets check if anything has it. and wasn’t renamed.
inurl:tunnel.nosocket.php ext:php
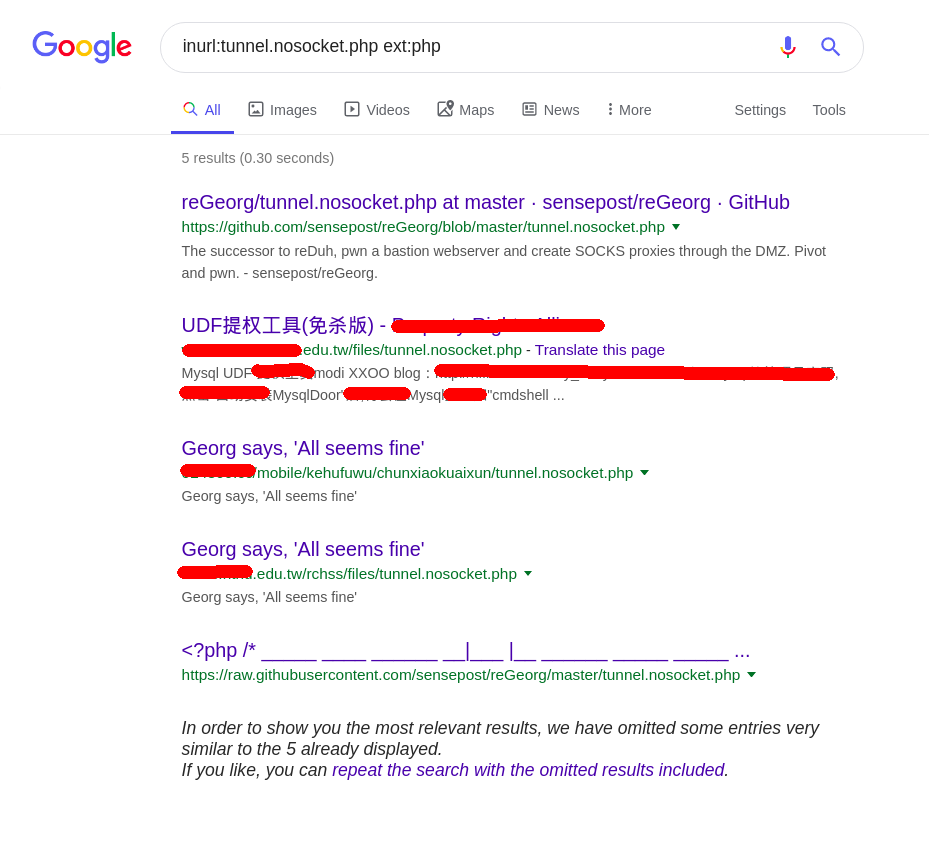
2 of the results are from github, 2 of them are actually pwned boxes (bad news for the webadmins), and 1 of them i have no idea because majority of the text is Taiwanese.
How Not to Store Your Company’s Usernames and Passwords
Lets check under https://docs.google.com/spreadsheets for “username and password”
site:https://docs.google.com/spreadsheets intext:password and username
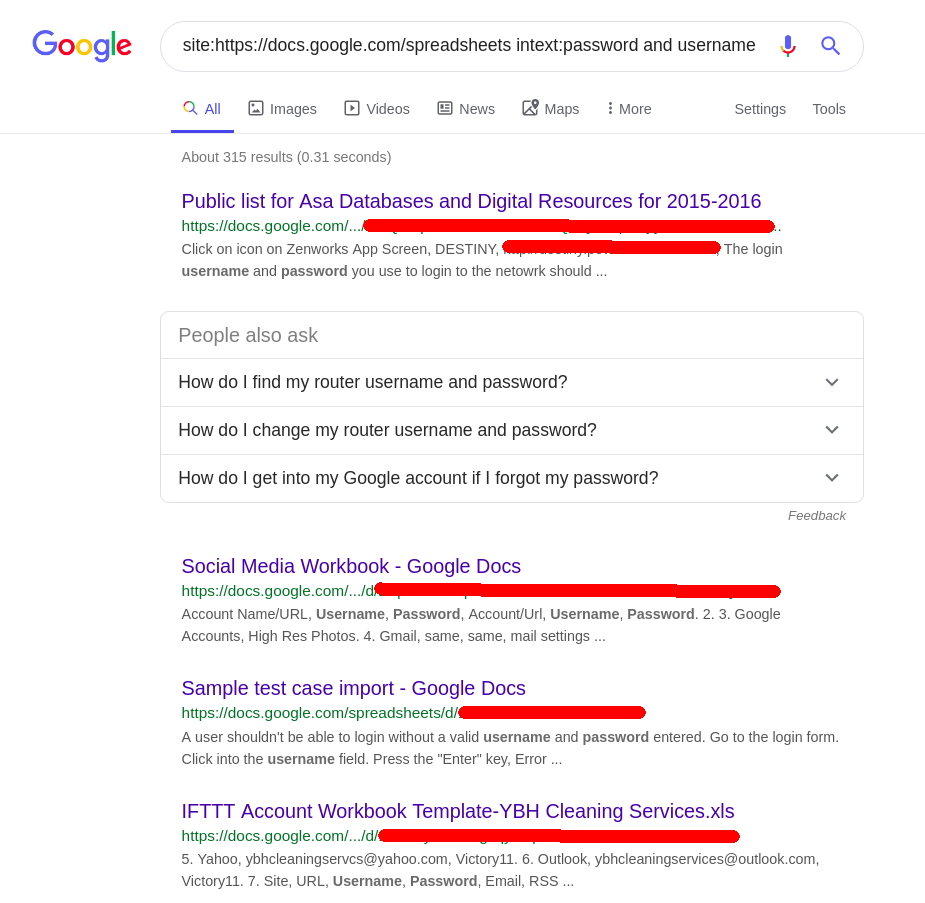
What could go wrong if we keep our social media username/passwords on a public excel file?
SSH key? Do i protect that?
Have you wondered how many people keep their ssh private keys public?
Well, there is only one way to know for certain. Lets just check the ones named “id_rsa”
intext:"-----BEGIN RSA PRIVATE KEY-----" inurl:id_rsa
Im not putting a screenshot, since pretty much everything here is sensitive.
But of course, people keep their private keys encrypted, i dont want to brute down passphrases. Lets just find the ones without a passphrase
intext:"-----BEGIN RSA PRIVATE KEY-----" -ENCRYPTED inurl:id_rsa
Bonus
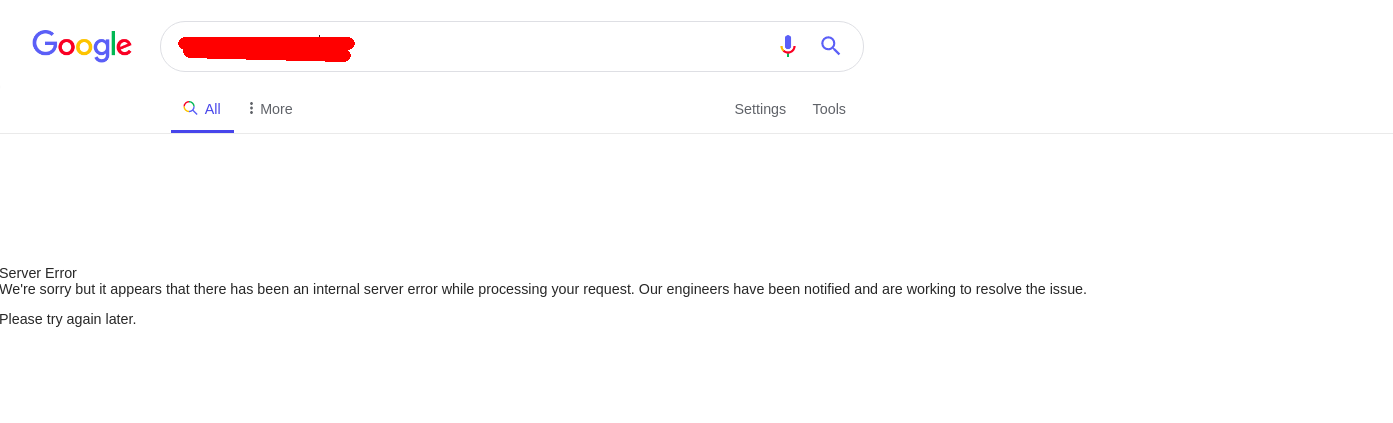
Crashing google
I can’t really reveal the query, but this query takes 10 seconds to respond, and responds with a server error. I have notified the google security team.