Generic In-game Currency Generator Trojan
25 Jun 2019Or “If you compile your trojan with debug, you leave your name in the binary”
Lets load this into gHidra, and see what is going on here
First of all, lets take a look into the strings, so maybe we can find something useful and skip analysing the binary
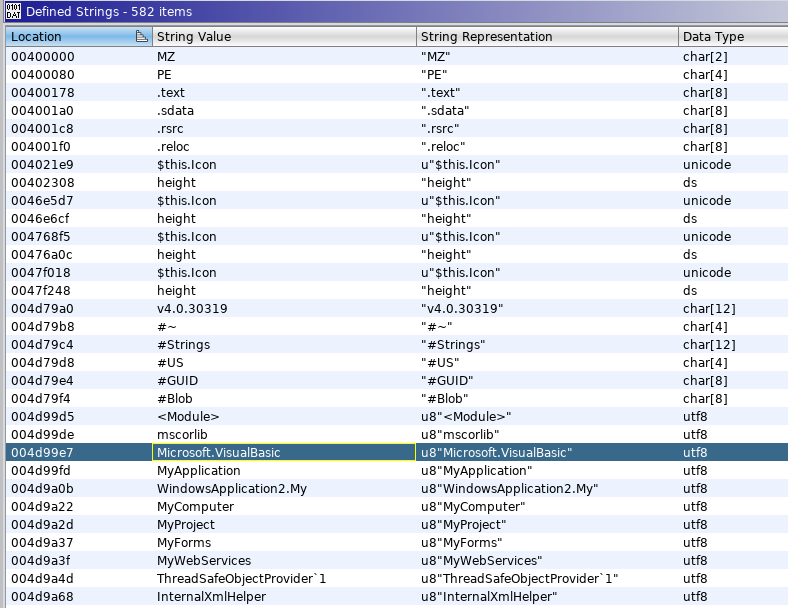
Visual basic… I feel like whenever i see a malware with vb, its bound do have something stupid in it
Wait, those are hardcoded keys! So you are not actually generating me the code? Who would have thought!
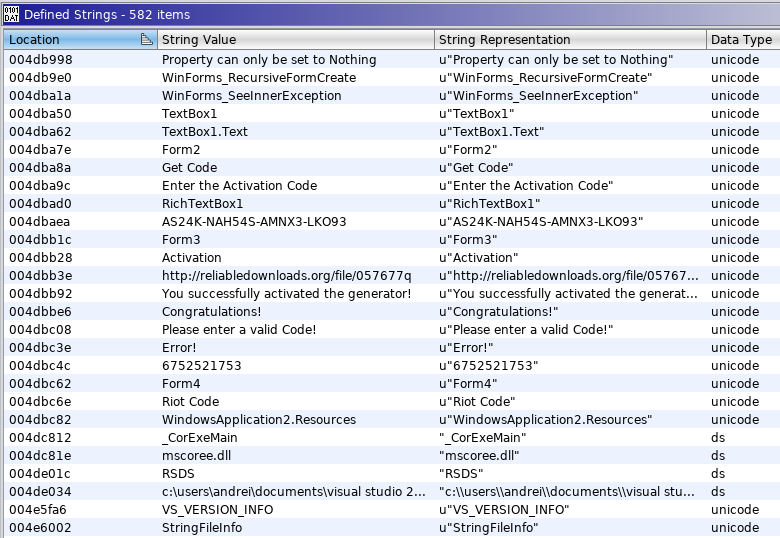
Also, there is a download link, im guessing its downloading the second stage, which is the actually malicious part
Wait wait wait, what’s that?
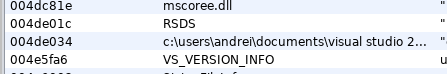
Congratz “andrei”, please keep compiling your malware with debug flag, so we can see your username from pdb path.
c:\users\andrei\documents\visual studio 2013\Projects\WindowsApplication2\WindowsApplication2\obj\Debug\WindowsApplication2.pdb
Anyway, lets check what the second stage is.
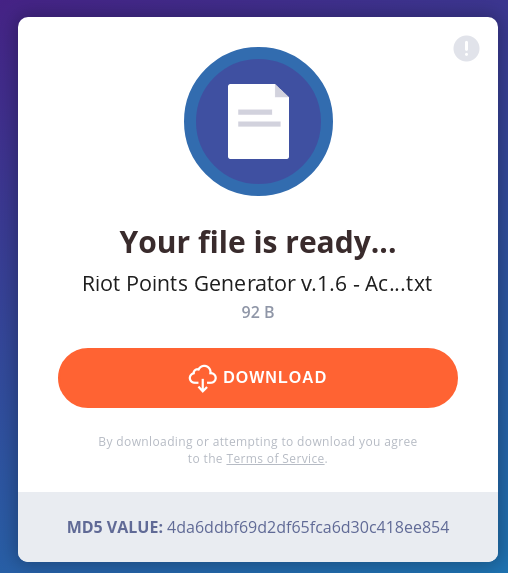
Its a…. txt?
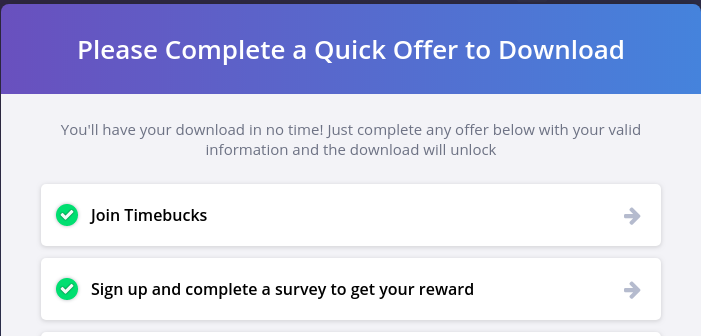
Wow, so you get your malware on a victims computer, and they are naive enough to run an exe they downloaded from some blogspot, and what do you do?
- You don’t give them the classic “Hey just enter your username and password!”
- You don’t just download a second malicious stage
- Lets be honest, if someone is naive enough to run this they would have just given the administrator permission if you asked,
You redirect them to a link which is just a “Complete this survey to get your file hurr durr”
Man, i don’t know if just don’t want to be a bad guy, or if you lack vision. I think im the only one that got robbed with this piece of junk, i want my 15 minutes analysing this back..
md5: a0b82e1b978bf5008930ca3c54926ff3 sha256: 839806ccc8fbeb9aef30a74498817ceab54a25eb1f4cf3fe61a5d415fcd610ef
